Organizations are developing strategies and creating roadmaps to implement and evolve Zero Trust (ZT) architecture. Many of these organizations suffer from vendor proliferation, overlapping capabilities and security gaps. There is a need to consolidate controls, enable interoperability and integrate technologies without compromising capabilities. Zero Trust Platforms (ZTP) enable ZT business and security results by offering a unified, comprehensive approach to operationalizing the ZT technology ecosystem. Whether in the early stages of the ZT journey or as key areas mature, ZTPs unite disjointed functions and provide additional capabilities and services to enrich cross-functional operations and simplify ZT adoption. No single solution can provide all the functionality required for an effective ZT architecture. ZTPs combine key ZT functionalities instead of requiring individual bolt-on tools. This establishes a more harmonious architecture through native and third-party integrations that don't seek to destroy and replace, but rather to anchor and focus.
- Simplify centralized management and user-friendliness. Many vendors claim centralized management, but few offer a universal user interface and user experience (UX) shared across multiple ZT components. Security and risk (S&R) professionals benefit from uniform visibility, management and implementation of controls that improve analysis, reduce complexity and enhance the analyst experience (AX). AX enhancement relies on streamlining analyst workflow and providing valuable training on tools and processes. Ease of use through centralized management enables S&R professionals and security analysts to discover, explore, classify, determine and execute without having to launch multiple user interfaces or other disparate consoles. Consolidation not only creates a unified control plane, but also provides native tools and services to assist, train and raise awareness of cyber hygiene, ensuring that ZT's best practices align with industry standards and requirements.
- Offer flexible deployment models supporting various hybrid architectures. Gone are the days when companies lived and operated within the confines of a traditional perimeter-based network defense. Organizations continue to adopt cloud-based software and services and migrate their resources to the cloud. Other organizations cannot migrate to the cloud or wish to retain some level of control by managing resources locally. Most organizations will be managing and securing hybrid architectures comprising on-premises and virtual environments for the foreseeable future. ZTP vendors are organizing their offerings to meet the needs of cloud, virtual and on-premises by offering flexible deployment modes for key security components that are manageable from a user interface hosted in the cloud or deployed locally to meet organizations' individual needs.
- Natively integrate ZTNA and/or microsegmentation capabilities. As core technologies or capabilities, Zero Trust Network Access (ZTNA) and microsegmentation implement the fundamental principles of ZT: apply least privilege, implicitly deny access and apply full visibility. ZTNA reduces dependency on existing VPNs by providing secure end-to-end access to cloud-based, SaaS and on-premises resources. Microsegmentation enables granular access control to assets and applications by creating microperimeters. These technologies enable organizations to deploy ZT controls with no negative impact on the workforce and business operations.
Evaluation summary
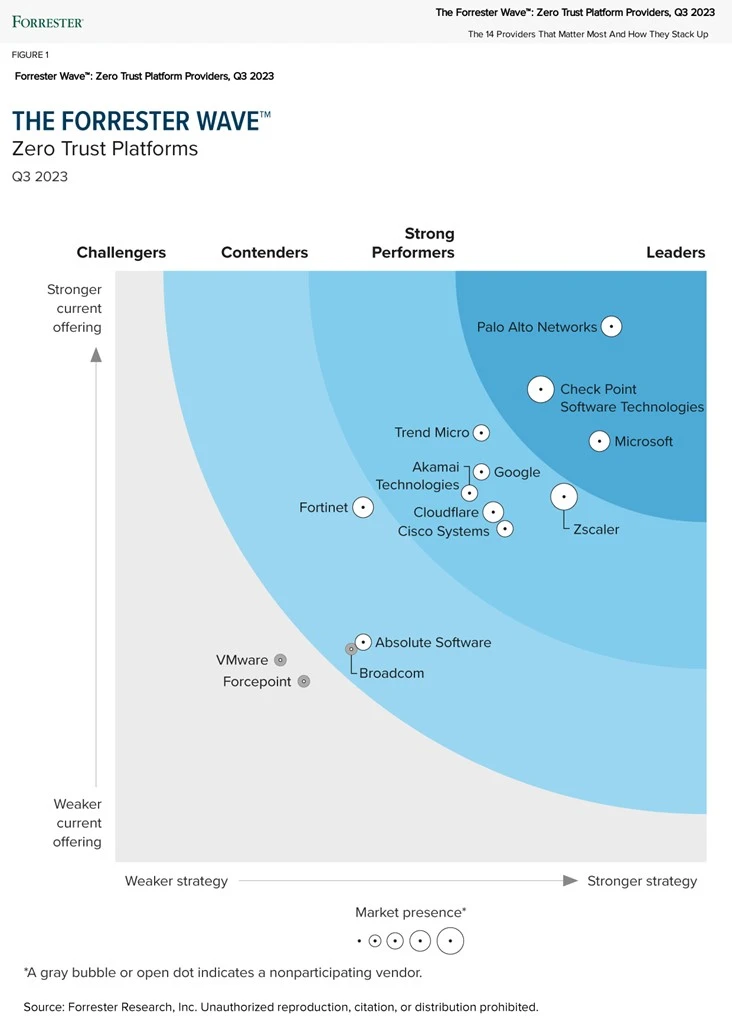
The Forrester Wave™ assessment highlights leaders, performers, contenders and challengers. It is an assessment of the best vendors in the market; it does not represent the entire vendor landscape. More information on this market can be found in the ZTP and ZT eXtended reports.
Supplier quotations

Supplier profiles
Forrester's analysis revealed the following strengths and weaknesses for each supplier.
Leaders
Palo Alto Networks' Zero Trust framework encapsulates the need to enable and protect a hybrid workforce. A reference customer hailed the value of enabling a dynamic, agile workforce to securely register, authenticate and access resources with Prisma Access, deployed as a service via the platform. Agent-based and agentless deployment options offer single sign-on (SSO) functionality that can support attributes from multiple identity and access management (IAM) solutions to organize and simplify the way users enter credentials and authenticate. However, the vendor's centralized management is not as consolidated as that of its competitors, and it is sometimes difficult to know what can and cannot be managed from a single user interface. Palo Alto's Zero Trust Framework is suitable for large, established companies on a ZT journey with a budget for high-end network and security capabilities.
- Microsoft's ZT promotion is reflected in its products and support services. Microsoft's modern, holistic approach to ZT has taken years. The vendor, along with other participants in this assessment, positions its cloud business as a ZTP, emphasizing its efforts to integrate ZT principles and methodology into Azure functionality. Its Copilot theme continues towards a notable vision of providing end-to-end, step-by-step guidance for ZT implementation while leveraging AI. This means that customers can follow their ZT journey with Microsoft at the same time. Microsoft further illustrates its vision through its roadmap, which includes Security Copilot and public previews of its ZTNA. ZT pricing and licensing that takes into account individual and disparate components within Azure, such as Sentinel, remains convoluted and requires a lot of time and effort to budget effectively.
Microsoft's ubiquitous presence compels it to align its SaaS capabilities with global standards, regulations and mandates. The publisher simplifies governance, notably with comprehensive data security, thanks to its classification and visibility of threats and risks. Microsoft complements the capabilities of the ZT ecosystem with integration and interoperability with third-party providers to provide granular control over data use and transmission. Microsoft's ZTP is a modest coupling of key solutions that do not fall entirely under its E5 license, as noted by reference customers, and currently lacks a compelling microsegmentation or true ZTNA solution. The supplier plans to finalize the development of these capabilities in its roadmap. Organizations already leveraging Microsoft E5 licenses for their security features are well placed to quickly start their ZT journey with add-on modules via Microsoft.
- Check Point Software raises the bar for centralized management and user-friendliness. The network security titan has been securing networks for just over 30 years with its hardware and software solutions. While many vendors are turning to an all-cloud offering, Check Point Software Technologies has kept an eye on current and future needs for ZT support in a hybrid architecture. Its ZTP components are deployed on site as hardware or software, in the SaaS cloud and virtually to meet unique architectural requirements. Although its investment in innovation is substantial, the vendor is focusing on mergers and acquisitions, leaving in-house R&D murky compared to its well-entrenched beginnings. Check Point's roadmap highlights network and security plans to develop AI and deep learning to improve detection and prevention of threat vectors.
Check Point's user interface offers a consistent experience, whether the administrator operates on the Infinity Portal or within individual components. Check Point Infinity Portal offers ease of use and simplicity to network and security professionals without the need to open multiple windows or tabs to perform daily tasks. Each component is centrally managed in a single management console and categorized into pillars to reduce complexity when navigating between different solutions. Check Point's microsegmentation capability leverages Azure to simplify network-level deployments, but lacks perceptible microsegmentation at the host level. The vendor has provided a reference customer that has not yet implemented ZTP. Larger companies with existing Check Point installations would do well to consider the additional features offered by the platform.
Strong Performers
- Zscaler offers seamless product security but lacks a consistent customer experience. At the height of the COVID-19 pandemic, Zscaler enjoyed great success with ZTNA and providing secure access to corporate remote workers, but struggled to defend on-premise use cases. The vendor's strategy to increase customer and market penetration aims to help customers maximize the value of their Zscaler deployments through training, customer success, product configuration and security audits, as well as the introduction of advanced features in entry-level bundles. The supplier proposes split messaging that includes the provision of seamless, secure information exchange and "zero touch, zero trust", the former representing a more realistic and achievable strategy. Its roadmap highlights enhancements covering several objectives, such as stopping cyberattacks using AI/ML to automate quarantine with remote browser isolation (RBI) and sandboxing.
Zscaler's Zero Trust Exchange (ZTP) combines its Secure Web Gateway (SWG), Data Loss Prevention (DLP), ZTNA and Cloud Access Security Broker (CASB) offerings. Its willingness to provide a software bill of materials (BOM) at contract signing enables customers to maintain product security with detailed information including SKUs, subcomponents and licenses. Zscaler has made efforts to consolidate via its Client Connector, which controls and manages Zscaler Internet Access (ZIA) and Zscaler Private Access (ZPA) via a single agent. However, ZIA and ZPA are still treated as separate components rather than as a single solution, creating a tedious customer experience: reference customers bemoan the fact that they are dealing with two separate consoles with "some overlap". What's more, Zscaler's Zero Trust Exchange remains a cloud-first solution with no real on-premise deployment options beyond its Branch Connector. Companies on the path to cloud migration with little or no need to support legacy systems can turn to Zscaler to start or advance their ZT journey.
- Trend Micro's Vision One improves AX through scanning, but sells less well than ZTNA . Trend Micro has come a long way from its humble beginnings as an antivirus solution. The cybersecurity software vendor has become something of an unsung hero of security monitoring and visibility of the network, endpoints and applications/workloads. The cost/value ratio offered by Trend through its native solutions and extensive integrations makes it a viable solution for budget-conscious customers. The vendor has been methodical with its Vision One strategy to operationalize ZT through advanced analytics. However, the vendor's secure access capabilities are under-utilized. Trend Micro's roadmap complements its vision by continually emphasizing improved visibility and analytics with modest secure access upgrades.
Visibility and advanced analytics are the strengths of Trend Micro's Vision One, enabling the vendor to deliver a robust AX. Reference customers appreciate the value of Vision One in optimizing visibility and control. Most of the information an analyst needs is accessible in a single console. This console provides a risk scoring metric based on user and device behavior that enables the creation of precise risk-based policies within the platform or in third-party solutions via integrations. Its ZTNA and SWG capabilities enable network-level microsegmentation for user-to-application control. The solution lacks the ability to take geolocation beyond IP-based, application-to-application communication to effectively apply microperimeters. Organizations beginning their ZT journey and in need of an advanced visibility and analytics solution to establish a baseline should evaluate Trend Micro.
- Google's BeyondCorp is the epitome of ZT, but companies need to embrace this vision. Technology titan Google has grown from a simple search engine to a leading cloud hyperscaler, security provider and ZT advocate that pioneered BeyondCorp. The vendor's commitment to innovation is underpinned by the continued expansion of its partner ecosystem and its commitment to advancing native capabilities. Its pricing and transparency are heavy-handed. It includes several models that force customers investing in Google's ZT vision to decide whether BeyondCorp Enterprise is suitable for a non-cloud-first business, or whether separate pay-per-use components of the global Google Cloud Platform are sufficient for hybrid and online businesses. local environments. Google's roadmap focuses on continued expansion of compliance coverage, partner integrations, cloud-native security capabilities and secure enterprise browsers.
Google's ZT approach demonstrates the effective application of the fundamental principles of the information security model. The vendor enables and protects hybrid workforces using Chrome on every device, offering agentless capability to secure and protect users and their interactions, regardless of location. Reference customers highlight the simplicity of supporting and managing Bring Your Own Device, particularly when combined with IAM and DLP offerings. With BeyondCorp Enterprise, administrators use disparate solutions under a single console to monitor and perform in-depth investigative actions. Google's ability to extend on-premises depends on the presence of Chrome or the ability to deploy an application connector to route traffic to its cloud enterprise. Google BeyondCorp Enterprise is ideal for organizations looking for cloud security solutions that leverage Google's cloud infrastructure and Chrome to secure the hybrid workforce.
- Cloudflare's innovation is boundless, but its change management is counterintuitive.As one of the youngest vendors in this evaluation, Cloudflare has demonstrated continued growth, moving from a humble online honeypot solution in 2009 to its official launch in 2010 and now to a fully cloud-native ZTP. The vendor's ZTP, Cloudflare One, unifies visibility and management of ZTNA, CASB, DLP and Web Application Firewall (WAF) with plans to continue adding and integrating more features and capabilities. Cloudflare's roadmap reflects the company's commitment to innovation, which takes a customer-centric approach to meeting growing trends and unique demands. The vendor's vision, however, is a rather familiar story: to become the control plane of choice for organizations.
As an access broker and domain name system reverse proxy, Cloudflare One succeeds in providing a centralized, consolidated platform to manage and orchestrate many of its native cloud solutions for ease of use and faster deployments. A variety of network, DLP and access control policies are managed from a single console, enabling customers to rapidly deploy and protect against Internet-born threats. Cloudflare's deployment modes are 100% SaaS-only, with connections to other cloud and on-premises resources facilitated only via application connectors alongside the existing architecture. Audit configuration management is cumbersome and unintuitive, with one reference customer describing it as "not comprehensive in scope" and having to sift through audit trails. Medium and large enterprises with a cloud-focused initiative to actively migrate resources and replace legacy WAN and VPN solutions should evaluate Cloudflare One.
- Akamai Technologies is a leader in microsegmentation, but its integrations lag behind.Akamai Technologies' acquisition of Guardicore in 2021 helped position the vendor as a viable ZTP supplier. The company is pursuing its M&A strategy to integrate more capabilities and complement existing ones, realizing its shared, if standard, vision of ZT simplification. Most attractive is the company's decision to create a dedicated ZT business unit (BU), headed by the former CEO of Guardicore, to enhance Akamai Technologies' capabilities and integrations with a ZT mindset. This BU is primarily aimed at internal R&D and does not provide much in the way of a dedicated support team for organizations starting out or actively implementing a ZT architecture. Akamai Technologies' roadmap reflects planned product enhancements to improve integration, coverage, scalability, ease of use and security.
Akamai Technologies' Zero Trust Security platform consists of its ZTNA, SWG and microsegmentation technologies, with integrations including its Multi-Factor Authentication (MFA) and WAF (Web application and API protection) solutions. Its Akamai Guardicore segmentation continues to be a winning asset for enterprises that value visibility and native firewall capabilities for microsegmentation. Reference customers have noted an improved UX for DevOps and security, as it "puts segmentation on top of something without having to re-architect the system". Akamai Technologies' technology ecosystem also integrates with third-party solutions. However, full native integration and feature parity have yet to surface. Reference customers have expressed dissatisfaction with the need to maintain multiple agents and separate support services. Organizations looking to reduce the stress of microsegmentation can benefit from Akamai Technologies' Zero Trust security platform.
- Cisco Systems has a broad product portfolio but no real centralized management.Cisco, a pillar of networking and security, has a long history of providing services to its customers. Its extensive partner ecosystem enables the vendor to expand purchasing opportunities for customers, while realizing the bulk of its SaaS bookings and revenues. Cisco's vision is to offer businesses better access control and security to thwart attackers. However, the vendor has yet to truly embody this vision in its broader platform, ultimately frustrating administrators trying to integrate existing architecture. Cisco's community strategy is remarkable, but struggles to gain traction: its ZT coverage is not as coherent or impactful as that of others. Its roadmap alludes to the eventual delivery of a consistent UX, but fails to ensure consolidation and centralized management.
Cisco's ZTP includes Duo, Identity Services Engine (ISE), Secure Client, Secure Workload, Umbrella and other Cisco solutions integrated through its pxGrid and product APIs. Duo efficiently applies the least privilege to all entities via context-sensitive policies. It now integrates with ISE without the need for a proxy, enabling consistent SSO with password-free MFA support for local and remote staff. However, the solution lacks true centralized management. Unlike the other companies participating in this evaluation, Cisco still has a fragmented control plane that requires a great deal of time and expertise to manage and maintain. Third-party integrations are notoriously difficult and have become a theme over the years, with one reference customer stating that this was "always" a challenge. The integration process isn't as smooth for third-party products that don't support pxGrid. Companies heavily invested in the Cisco technology ecosystem should consider the ZTP provider.
Contenders
- Best known for its firewalls, Fortinet has since expanded its coverage through strategic acquisitions and some organic growth. Fortinet's vision focuses on network and security operations center (SOC) interoperability, with an emphasis on interoperability between the many components offered by the vendor. Fortinet falls short with its community, offering little or no peer-to-peer discussion, advice or awareness of ZT's advancement beyond its product's capabilities. Its roadmap is disappointing, providing feature updates and entry-level capabilities focused on the ZT pillar that are tied to what it calls "neural network learning", which leverages AI/ML and analytics. While the vendor is known for delivering value at low cost, the FortiFlex points-based system makes a thud for a pricing model that makes sense on paper.
Fortinet's components all leverage FortiOS, which is highly regarded for its ease of use, implementation and management, reducing the need for administrators to relearn disparate user interfaces for multiple components. This translates into its platform that optimizes network security, enabling administrators to gain greater visibility and control of FortiGates and FortiAnalyzer in cloud, virtual and on-premises environments centrally via FortiManager. Fortinet shines in on-premises environments and can support hybrid networks. However, cloud deployments are not as conclusive, with one reference customer noting that capabilities - such as CASB - are not fully developed, affecting its ability to provide effective workload and application security. Companies of all sizes with multiple Fortinet network security solutions will benefit from the FortiManager component of the vendor's ZTP offering.
- Absolute Software's self-healing security is promising, but new innovations are rare. Absolute Software was ahead of its time, becoming the only factory-integrated cybersecurity software for endpoints. Having enjoyed success in the education sector, the company diversified into other public and private market sectors. Crosspoint Capital completed the acquisition in July 2023, taking the supplier private. Absolute Software's vision of resilient, self-healing security is as unique as its capabilities for automating the restoration of endpoint and network connectivity. However, the vendor offers little in the way of innovation, relying on its reputation rather than aligning itself with current trends and future needs. Absolute Software's roadmap is straightforward, focusing primarily on table stakes enhancements to improve monitoring with AI, reduce the attack surface and ease deployment.
The Absolute Zero Trust solution builds on the vendor's Secure Endpoint and Secure Access solutions, integrating tightly with its SWG. Because it is integrated into devices by default, the vendor is well placed to provide effective data and device security for managed devices by relying on a single agent to enforce access and compliance policies at the endpoint level. Reference customers praise its effectiveness in protecting and securing remote workers and devices. Absolute Software requires endpoints to install and/or register the agent on devices, but unmanaged endpoints have no real agentless or clientless alternative for limited or just-in-time/just-enough access to resources. Absolute Software does not prioritize data-at-rest security, offering only full disk encryption via third-party integration. Organizations with more restrictive requirements wishing to extend network access control capability to the end point should evaluate Absolute Software.
- Broadcom offers broad coverage and an ambiguous vision for its platform. Broadcom's acquisitions of CA Technologies and Symantec have effectively created a one-stop shop for all things security. The vendor's overall market approach is to focus on a limited set of very large organizations, which initially led to a mass exodus of smaller customers to other vendors. The vendor's ZTP strategy lacks a definitive long-term outlook and maintains a level of segregation of its security offerings into individual segments with short-term enhancements that are more reactionary than innovative. Broadcom's roadmap does, however, seek to integrate internal product families into a platform via a unified Symantec console scheduled for release in 2024, in the hope of attracting new customers.
Broadcom's Symantec ZTP includes mature products such as CASB; cloud security gateway (CSG); ZTNA; identity, credentials and access management; endpoint; and DLP with several deployment options, including cloud, on-premises and hybrid networks. The CSG and CASB components are particularly noteworthy, with reverse proxy and extended application coverage available without the need for third-party integrations. DLP functionality offers customers the ability to perform endpoint, cloud or on-premises analysis, creating the possibility to meet specific deployment requirements in complex environments. The user interface is easy to understand but dated. Broadcom declined to participate in the full Forrester Wave evaluation process.
Challengers
- Forcepoint progresses with ZTE elements but leaves other aspects aside. Forcepoint, originally founded as a reseller in 1994, has transformed itself through mergers and acquisitions to become a security platform provider focused on data security, ZTNA, SWG and RBI. More recently, the supplier sold its government business to TPG, following its acquisition by Francisco Partners from Raytheon Technologies. Forcepoint's strategy focuses primarily on enhancing its Zero Trust Edge (ZTE) offering, while leaving aside other ZTP aspects such as its hardware solutions for maintaining stronger on-site network security. Forcepoint lags behind in innovation, focusing on integrating acquisitions and creating solutions to meet current market needs.
Forcepoint offers several products in the ZTP space, such as data classification, DLP, user behavior analysis, ZTE and firewalls. Functionality is comparable to that of other vendors in the field, but lags behind from a platform point of view, as the onus is on SOC analysts to correlate disparate telemetry information. Multiple consoles are required to build a picture, resulting in an extremely manual process for analysts when provisioning or responding to an incident in real time. Forcepoint's existing customers and medium to large enterprises would benefit from evaluating this combined offering. Forcepoint declined to participate in the full Forrester Wave evaluation process.
- VMware is best known for offering the flexibility to deploy virtual machines just about anywhere. The vendor's vision is linked to ZT and the ability to provide coverage across multiple pillars of the ZT model. VMware's installed base in most organizational departments (e.g. security, enterprise IT and vendor virtual machine-based offerings) provides in-depth insight into virtual networks and endpoints through network security solutions that include its NSX software-based firewalls. Its acquisition of Carbon Black has enabled it to add an endpoint detection and response (EDR) component to its offering, extending its endpoint security coverage. The roadmap lags behind other assessments and makes some improvements to VMware-specific features, including additional third-party integrations and EDR enhancements for Carbon Black. Broadcom's imminent acquisition of VMware could also have an impact on the vendor's strategy, roadmap and go-to-market approach, if Broadcom's previous acquisitions are any indication of the way forward.
VMware's workload protection capabilities are widely used in cloud, multicloud and hybrid deployments, and have become the de facto standard for cloud migrations. Cloud configuration management, security, governance and lifecycle management all feature prominently in product offerings. However, VMware offers no true ZTP solution that unifies its disparate solutions. Organizations using VMware solutions, particularly for virtualized environments or with self-hosting requirements, should investigate VMware's ZTP offering. VMware declined to participate in the full Forrester Wave evaluation process.
Evaluation overview
- Current offering. Each vendor's position on the vertical axis of the Forrester Wave graph indicates the strength of its current offering. Key criteria for these solutions include network security, total ecosystem, centralized management, visibility and analytics, automation and orchestration, device security, AX and integrations.
- Strategy. Placement on the horizontal axis indicates the strength of suppliers' strategies. We evaluated vision, innovation, roadmap, partner ecosystem, adoption, as well as pricing flexibility and transparency.
- Market presence. Represented by the size of the markers on the graph, our market presence scores reflect each supplier's total sales for the product and number of current customers.
- Strong enterprise support for ZTP functionality. Vendors must natively provide basic ZTP functionality across a minimum of four ZT (pillar) domains, and must include ZTNA and/or microsegmentation capability. Vendors must also have recent and ongoing adoption among enterprise customers of ZT functionality that can operate in on-premises, cloud and hybrid environments.
- A ZT product generally available from May 25, 2023. Forrester did not take into account any features released after May 25, 2023. All features were generally available for purchase, not as beta or limited versions. The platform was delivered as a product or software as a service, not as a managed service.
- A platform that meets at least three main ZT use cases. ZTP must provide a solid foundation for addressing three or more primary use cases in a heterogeneous environment that include enabling and protecting hybrid workforces, monitoring and securing network traffic across the enterprise, preventing lateral movement of unauthorized activity, applying least privilege to all entities, and centrally managing key security controls.
- Mindshare among Forrester's corporate customers. The solution has generated interest, in the form of mentions and inquiries, among Forrester's customer base over the past 12 months; end-users frequently mention the product's shortlisting; and other vendors mention the evaluated vendor as a frequent competitor in the market.
- Substantial ZT revenues. We required suppliers to have generated at least $200 million in annual revenues on the ZT platform market over the last four quarters in at least two geographical regions.
- ZT advocacy. Suppliers are progressing, engaging and leveraging the operationalization of ZT as an ecosystem to meet growing customer needs and challenges that include applying ZT concepts and principles internally via solutions that are part of a commercialized ZTP.
Source: Forrester
Share on :







